If you are an XP user experiencing infections again and again, you might want to disable the Windows autorun feature. Autorun allows downloaded files to open immediately upon download. That may sound like a good thing to most of you, but what if the file downloaded is cornflicker? Not so good. Firefox, Safari, Chrome, and Opera (my favorite for general web browsing because of the speed) download to a location on your computer which allows your autoprotect in your antivirus to catch bad-guy files.
The good news is Microsoft did disable this autorun.inf file in Vista and 7. You have to give Microsoft credit for this. It's not as convenient for the user, but in the long run it saves the user computer maladies.
Please refer to the Microsoft article below for instructions how to disable the autorun feature on your XP system.
http://support.microsoft.com/kb/967715/
Greetings!
What's the Matter? Didn't you have anyone in pink pumps fix your computer before?
Friday, May 28, 2010
Thursday, May 27, 2010
What is Microsoft.Net?
Microsoft.Net is a collection of code used for surfing the Internet. It consists of libraries of code for low-level programming tasks. It layers over the operating system for web applications. Some PDF generators need this program to generate PDFs within a web application. It helps web programmers to build web programs faster, because they are "borrowing" code. It can be used in many types of application and that is why it has a huge appeal to programmers.
It is safe to download directly from Microsoft. Here is the link:
http://www.microsoft.com/downloads/details.aspx?FamilyID=0856EACB-4362-4B0D-8EDD-AAB15C5E04F5&displaylang=en
It is safe to download directly from Microsoft. Here is the link:
http://www.microsoft.com/downloads/details.aspx?FamilyID=0856EACB-4362-4B0D-8EDD-AAB15C5E04F5&displaylang=en
Wednesday, May 26, 2010
File Format Explanations
PNG portable network graphics. Editable in Photoshop and Corel Paint Shop Pro. Viewable in all browsers. Best feature: super-duper compression.
DLL dynamic link library. These are system files that are used in conjunction with other programs. You can't edit them directly.
EXE executable file. This is an instruction to execute a program. You can't edit EXE files in Word or view them in your web browser.
FLV flash video. This video type can be used in Google video and Youtube. Best feature: you don't need a special player; it works thru Adobe's software which you already have installed on your computer.
RAR roshal archive file. It's named for its creator, Eugene Roshal. It's used for file compression. Rar files can wrap up several files in one nice little package. You can open them with WinRAR. Best feature: the resulting file is a fraction of the original size.
RTF rich text format. It's a word-processing format. Best feature: it works in many programs and operating systems.
ZIP another compression format. It is done thru a zip program (Winzip, 7zip, or PKzip to name a few) and it provides minimal compression.
TMP temporary file. When downloading web pages each part stores as a temp file on your computer. They are not meant to be opened. Usually it's safe to delete temp files. It's best to delete temporary internet files in the web browser rather than in Windows Explorer. Other programs can also create temp files.
MP4 motion picture expert group is an audio/video file. Playable in media players and on portable devices.
DLL dynamic link library. These are system files that are used in conjunction with other programs. You can't edit them directly.
EXE executable file. This is an instruction to execute a program. You can't edit EXE files in Word or view them in your web browser.
FLV flash video. This video type can be used in Google video and Youtube. Best feature: you don't need a special player; it works thru Adobe's software which you already have installed on your computer.
RAR roshal archive file. It's named for its creator, Eugene Roshal. It's used for file compression. Rar files can wrap up several files in one nice little package. You can open them with WinRAR. Best feature: the resulting file is a fraction of the original size.
RTF rich text format. It's a word-processing format. Best feature: it works in many programs and operating systems.
ZIP another compression format. It is done thru a zip program (Winzip, 7zip, or PKzip to name a few) and it provides minimal compression.
TMP temporary file. When downloading web pages each part stores as a temp file on your computer. They are not meant to be opened. Usually it's safe to delete temp files. It's best to delete temporary internet files in the web browser rather than in Windows Explorer. Other programs can also create temp files.
MP4 motion picture expert group is an audio/video file. Playable in media players and on portable devices.
Tuesday, May 25, 2010
I Destroy Rogues!
On an almost daily basis, I find myself battling rogue antivirus infections. They are not always avoidable and sometimes pesky to remove. Best case is 1 hour (like today!); usual case 4 hours; worse case 7 and worst case is the computer has to be reimaged (wiped and start over again).
Rogues are scareware: they scare you into downloading and paying for them. Don't pay these crooks!
To avoid: don't log on with administrative priviliges, use a safer browswer (not IE), don't use msn as your home page and update everything all the time.
To fix: go into safe mode, download malwarebytes antimalware, update and scan. Sometimes processes are running that don't allow this. That's when you need the help of a technician. You don't want to end processes that can cause instability of your system.
After a rogue infection is cleaned: change passwords on all internet accounts. Your information may have been hijacked and it's a good idea to change passwords just in case. It's easy to remember a new password and not so easy to recover from an identity theft.
Rogues are scareware: they scare you into downloading and paying for them. Don't pay these crooks!
To avoid: don't log on with administrative priviliges, use a safer browswer (not IE), don't use msn as your home page and update everything all the time.
To fix: go into safe mode, download malwarebytes antimalware, update and scan. Sometimes processes are running that don't allow this. That's when you need the help of a technician. You don't want to end processes that can cause instability of your system.
After a rogue infection is cleaned: change passwords on all internet accounts. Your information may have been hijacked and it's a good idea to change passwords just in case. It's easy to remember a new password and not so easy to recover from an identity theft.
Friday, May 21, 2010
Shake shake shake... that window!
A windows 7 feature that you might not now about is Aero Shake. Simply shake the window that you want to work on and every other window will minimize instantly. Just grab the window and shake, shake shake!
Aero peek is an instant view of your desktop and it's open windows. Hover your cursor over the rectangle in the lower right corner of your screen.
Both of these features are in Windows 7 only; sorry Vista and Xp users!
Aero peek is an instant view of your desktop and it's open windows. Hover your cursor over the rectangle in the lower right corner of your screen.
Both of these features are in Windows 7 only; sorry Vista and Xp users!
Thursday, May 20, 2010
What's the Difference Between a Bug and a Virus?
They are both code, but that is where their similarities end.
A virus is a successfully written chunk of code with malicious intent. It can wipe out data or send it to another person. It can rob memory resources and affect the performance of your computer. A virus needs to be removed with an antivirus program or cleaned by a technician or skilled user.
A bug is unsuccessfully written, benevolant code. Its intent is to enhance program content or functionality, but the code did not blend with your operating system, browser, or add-ons. There is nothing you can do about this type of error. Restarting your computer might help you to regain functionality of the program, but your computer isn't in danger of being wiped out.
I've been experiencing a bug in Facebook error and restarting resolves my browsing ability, but the error hasn't been corrected so it will continue until the code is rewritten.
A virus is a successfully written chunk of code with malicious intent. It can wipe out data or send it to another person. It can rob memory resources and affect the performance of your computer. A virus needs to be removed with an antivirus program or cleaned by a technician or skilled user.
A bug is unsuccessfully written, benevolant code. Its intent is to enhance program content or functionality, but the code did not blend with your operating system, browser, or add-ons. There is nothing you can do about this type of error. Restarting your computer might help you to regain functionality of the program, but your computer isn't in danger of being wiped out.
I've been experiencing a bug in Facebook error and restarting resolves my browsing ability, but the error hasn't been corrected so it will continue until the code is rewritten.
Wednesday, May 19, 2010
UPS Delivers.... Electricity!
UPS in computer hardware lingo mean uninterruptible power supply. If the electricity to your computer fails, a UPS can provide battery power long enough for you to save documents. UPS can save not only your work, but your computer. If you live in a building that has power problems and your computer constantly loses power, your hard drive can be damaged to the point it won't boot.
UPS's vary in size and length of time they provide power. The one I am using is about the size of a shoebox, but the battery inside it is only about the size of a pound of butter. Physical size doesn't matter as much as length of time. You should never plan on using a UPS for an extended period of time. All electricity is not the same. Only use a UPS to provide temporary power long enough to get your work saved and your computer properly powered down.
APC is one of the most popular providers of UPS power. Here's a look at one of their personal UPS backup solutions: APC Back-UPS ES 8 Outlet 550VA 120V. Here's a UPS from one of their competitors: CyberPower CP1000AVRLCD 9-Outlet Intelligent LCD UPS (1000VA/600W)
CyberPower CP1000AVRLCD 9-Outlet Intelligent LCD UPS (1000VA/600W)
One rule of thumb when using UPS protection: only essential appliances get plugged into UPS outlets. Printers are not essential for shutting down a computer so they do not get plugged into UPS power supplies. Even though a monitor is a big power hog, it needs to be plugged into the UPS because you can't see the screen to shut down the computer.
UPS's vary in size and length of time they provide power. The one I am using is about the size of a shoebox, but the battery inside it is only about the size of a pound of butter. Physical size doesn't matter as much as length of time. You should never plan on using a UPS for an extended period of time. All electricity is not the same. Only use a UPS to provide temporary power long enough to get your work saved and your computer properly powered down.
APC is one of the most popular providers of UPS power. Here's a look at one of their personal UPS backup solutions: APC Back-UPS ES 8 Outlet 550VA 120V. Here's a UPS from one of their competitors:
One rule of thumb when using UPS protection: only essential appliances get plugged into UPS outlets. Printers are not essential for shutting down a computer so they do not get plugged into UPS power supplies. Even though a monitor is a big power hog, it needs to be plugged into the UPS because you can't see the screen to shut down the computer.
Monday, May 17, 2010
What's a Firewall and How Much Firewall Do You Need?
A firewall is a security device that blocks Internet traffic coming in or out of a computer or network. This can be accomplished by a software firewall or it can be done using a hardware firewall.
Everyone needs a firewall to prevent malicious hackers from wiping out their valuable data. The question is how much firewall does one need?
Not as much as one might expect.
Windows has a built-in firewall. In many cases, the Windows firewall is sufficient for a busy agent.
I don't like to brag (except maybe a little), but the firewall at my work is pretty tight. If you are plugging your laptop into a port at one of our offices, you don't need anything more than anti-virus and the Windows Firewall running. If we have a firewall and you use your firewall, you will notice slow browsing and internet application performance. It's kind of like wearing 2 raincoats. One really is enough. If you notice sluggishness in the office, turn off your firewall.
At your home, you need to consult with your isp (internet service provider) to see that they are providing some type of firewall protection to you. If they are, then maybe you should reconsider your current firewall protection plan. With most home ISPs, you'll usually use equipment like a modem or router that has built in firewall protection. This is a hardware firewall.
The alternative is a software firewall. Whichever one you choose, what you need to know is, how to allow exceptions to your firewall. An exception is an internet address that you want to allow through a "hole" in your firewall or one that you wish to block such as an entire domain, like limewire.com. Any objectionable website can be blocked by domain name or by IP address.
With a software firewall such as the one that comes installed with Windows, you can set alerts that will notify you when online if you navigate to what it considers a suspicious site. You would notice messages popping up asking to ALLOW or BLOCK. You must evaluate each message and determine if it's a legitimate security risk or not. 95% of the time, problems connecting to a wireless is due to a 3rd party firewall objecting to it (especially Norton 360 and Trend Micro). Turn them off (or better yet uninstall) and the wireless magically starts to work!
Everyone needs a firewall to prevent malicious hackers from wiping out their valuable data. The question is how much firewall does one need?
Not as much as one might expect.
Windows has a built-in firewall. In many cases, the Windows firewall is sufficient for a busy agent.
I don't like to brag (except maybe a little), but the firewall at my work is pretty tight. If you are plugging your laptop into a port at one of our offices, you don't need anything more than anti-virus and the Windows Firewall running. If we have a firewall and you use your firewall, you will notice slow browsing and internet application performance. It's kind of like wearing 2 raincoats. One really is enough. If you notice sluggishness in the office, turn off your firewall.
At your home, you need to consult with your isp (internet service provider) to see that they are providing some type of firewall protection to you. If they are, then maybe you should reconsider your current firewall protection plan. With most home ISPs, you'll usually use equipment like a modem or router that has built in firewall protection. This is a hardware firewall.
The alternative is a software firewall. Whichever one you choose, what you need to know is, how to allow exceptions to your firewall. An exception is an internet address that you want to allow through a "hole" in your firewall or one that you wish to block such as an entire domain, like limewire.com. Any objectionable website can be blocked by domain name or by IP address.
With a software firewall such as the one that comes installed with Windows, you can set alerts that will notify you when online if you navigate to what it considers a suspicious site. You would notice messages popping up asking to ALLOW or BLOCK. You must evaluate each message and determine if it's a legitimate security risk or not. 95% of the time, problems connecting to a wireless is due to a 3rd party firewall objecting to it (especially Norton 360 and Trend Micro). Turn them off (or better yet uninstall) and the wireless magically starts to work!
Friday, May 14, 2010
Where Can I Get Office for Free?
http://www.openoffice.org/ is the place to download a free office productivity suite. What's the catch? There is none. It's free. You can put it on as many computers as you like. It's a lengthy download (276 MB), but that's because it's a full office suite.
Here's what you get for nothing:
Here's what you get for nothing:
- Word Processor with many of the tools that you need (mail merge, tables, ability to export to PDF)
- Presentation Program with many choices (backgrounds, charts, custom slide show settings)
- Database Program that is user friendly and has many options to help keep track of your customers
- Spreadsheet Program with the functions you need (charts, formulas, graphics)
- Drawing Program with features most home users want (tools and special effects)
- Formula Editor for making macros
- Template Organizer for storing your custom templates
Wednesday, May 12, 2010
What is Legacy Hardware/Software?
Legacy means out-of-date hardware or software. It's something that should be replaced by newer software or hardware. If you get a new computer and phone HP for assistance hooking up your 10 year old printer to it, a tech might say something like "Windows 7 doesn't support legacy hardware." It's a polite way to tell you it needs to be replaced. When a piece of hardware gets old, drivers for new operating systems become scarce. At that point it's time to recycle/donate the hardware. The same is true for operating systems. If you get a new printer and call to get your Windows 2000 computer hooked up to it, the tech might say "Legacy OS's aren't supported."
You might be thinking, "OH they JUST want more MONEY." Well, not really. Processor manufacturers keep developing new processors and the hardware and OS requirements go up, up, up! So if you hear this term from a vendor, don't think of legacy hardware/software as an insult, but as an encouragement to stay up to date with technology so you can get your work done in the most efficient manner.
You might be thinking, "OH they JUST want more MONEY." Well, not really. Processor manufacturers keep developing new processors and the hardware and OS requirements go up, up, up! So if you hear this term from a vendor, don't think of legacy hardware/software as an insult, but as an encouragement to stay up to date with technology so you can get your work done in the most efficient manner.
Thursday, May 6, 2010
Is it Spam or Junk Mail?
They are the same animal, just one is client side and one is server side.
Client side email filtering requires the person to set up rules and the email client must be open in order for the filtering to take place because it is done with the email client. For example, junk email in Outlook is an example of client side filtering. It takes a lot work on the part of the person using the email.
Spam filtering is a server side filtering system. It's always working so it's always effective.
I recommend if you are using an email client such as Outlook or Thunderbird, that you use your webmail interface to alter spam settings and not your email client's junk filter. Also if your computer crashes and you have set up junk mail filtering, your filter will be lost unless it has been backed up.
Client side email filtering requires the person to set up rules and the email client must be open in order for the filtering to take place because it is done with the email client. For example, junk email in Outlook is an example of client side filtering. It takes a lot work on the part of the person using the email.
Spam filtering is a server side filtering system. It's always working so it's always effective.
I recommend if you are using an email client such as Outlook or Thunderbird, that you use your webmail interface to alter spam settings and not your email client's junk filter. Also if your computer crashes and you have set up junk mail filtering, your filter will be lost unless it has been backed up.
Wednesday, May 5, 2010
Is Your Firmware Up to Date?
Firmware is used to describe small programs that are not changeable (except for updates) inside an electronic device. Your television remote has firmware even, but I'm not concerned about someone hacking into that and changing the channel on you. Cameras have firmware, cell phones have firmware, printers have firmware, but what I am most concerned about is your wireless router. Firmware updates are released to patch security holes in a vendor's firmware. Most home users never update their firmware and aren't even aware that it needs to be updated.
Now you know. What are you going to do? Well, firmware is product specific. If you are concerned about your particular device, check the vendor's website to see if they have firmware updates and follow their instructions on how to apply it. If you have problems applying the firmware, contact the vendor. If you receive your appliance from your ISP, contact your ISP for instructions on how to do this. You do not want to wipe out their specific settings, so follow their instructions carefully.
Now you know. What are you going to do? Well, firmware is product specific. If you are concerned about your particular device, check the vendor's website to see if they have firmware updates and follow their instructions on how to apply it. If you have problems applying the firmware, contact the vendor. If you receive your appliance from your ISP, contact your ISP for instructions on how to do this. You do not want to wipe out their specific settings, so follow their instructions carefully.
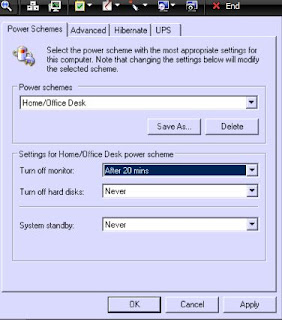
Is Your Computer Narcoleptic?
Does your computer fall asleep? Check your power settings in Control Panel. Make sure that they are set the way you need them to be. Utilizing sleep mode is a good thing but only if your motherboard and graphics card supports it. If your monitor doesn't seem to want to wake up, then don't let it go to sleep. Adjust your power setting to "Never."
If both your motherboard and graphics card support waking up, then I suggest 20 minutes or less for your monitor's power setting.
If both your motherboard and graphics card support waking up, then I suggest 20 minutes or less for your monitor's power setting.
Failure to UPDATE! (Don't let psychos in!)
If you were to get a report card based on your computer maintenance, what grade would you give yourself? Running scans is good, but without updating you can miss something important. Case in point: the insane man who tried to build a car bomb in my home state. Had Emirates updated their no-fly list they would not have admitted a psycho guy on their plane. See how important updating is??? Emirates happens to be my favorite airline to fly as it is quite comfortable even in coach which I always fly, but that was a big mistake on their part. Don't they want to punish the psychos? How could they be so careless, psychos are dangerous
If whichever program you are using for malware, adware and viruses doesn't automatically update, you need to make it part of your habit to click UPDATE before running a scan. You don't want dangerous psychos gaining access to your computer.
How often you should run scans is based on your web usage. Not just how much you use it but what types of sites you visit. If you are on Facebook all day, run a daily scan. If you are strictly on SSL sites then maybe once a week. When you do your next scan, remember the psycho almost got away. Don't let psychos get away in YOUR computer.
Regards,
Janet
If whichever program you are using for malware, adware and viruses doesn't automatically update, you need to make it part of your habit to click UPDATE before running a scan. You don't want dangerous psychos gaining access to your computer.
How often you should run scans is based on your web usage. Not just how much you use it but what types of sites you visit. If you are on Facebook all day, run a daily scan. If you are strictly on SSL sites then maybe once a week. When you do your next scan, remember the psycho almost got away. Don't let psychos get away in YOUR computer.
Regards,
Janet
Tuesday, May 4, 2010
Windows 7 Documentation
Or lack of it! It comes with a steep pricetag, but no printed documentation. Help files are available online in limited form. A new book by David Pogue is available for under 30$ shipped from Amazon.
Windows 7: The Missing Manual
If you need help with Windows 7, you might want to pick up a copy!
Windows 7: The Missing Manual
If you need help with Windows 7, you might want to pick up a copy!
What's a Tech Gal Think About Office 2010?
Really it's not scarey different than 2007, and it does have some features that you might be interested in.
I don't like how long it takes to open an Office 2010 application, but I am hoping they'll resolve that before releasing it from public beta testing.
To get the cheapest price on it: buy as soon as it comes out. The price will skyrocket.
See also: http://janetperkinstech.blogspot.com/2010/04/need-office-2007-for-home.html for information about buying Office 2007 with a free upgrade to 2010.
- Built-in screen capture tool in Word. It's easy to use.
- When opening Outlook for the first time, it gives the option to configure a phone for email. If your life revolves around your phone and not your computer, this might be a feature you'll like.
- Inserting videos in PowerPoint presentations is easy in Office 2010.
- A Hide Ribbon option is available if you need to work on a long document.
- New Smart Art templates. Ok, they are corny, but I like them. :)
- Outlook 2010 utilizes Windows 7 jump lists. If you do something over and over again in Outlook, then you probably will like this feature. Pinning a repetitive task to the taskbar just makes life a little easier. ;)
- Background removal tool that is pretty slick. I'm not a graphic designer and find most graphic design tools cumbersome. I like easy; this is easy.
- Author permissions has been modified. It's become much more complex which is good for people who are file sharing in an office.
I don't like how long it takes to open an Office 2010 application, but I am hoping they'll resolve that before releasing it from public beta testing.
To get the cheapest price on it: buy as soon as it comes out. The price will skyrocket.
See also: http://janetperkinstech.blogspot.com/2010/04/need-office-2007-for-home.html for information about buying Office 2007 with a free upgrade to 2010.
Monday, May 3, 2010
Computer Mistakes That Will Cost You Money
Here's a list of No-No's that will end up costing you money. I've seen all these done and most were done recently. Hope you don't do any of these!
- Ignoring an overheating problem. If your computer is hot to the touch, get it checked before your processor is fried.
- Unplugging non-USB devices with the power on.
- Not inspecting the connection before trying to plug a cable in. Make sure you look at the connection and don't force it in.
- Not using surge protection.
- Not cleaning the power supply fan
- Using a data vacuum INSIDE the computer
- Not shutting down properly
- Magnets on the metal computer case
- Not using updated antivirus and running regular scans. Macintosh users please don't be lulled into a false sense of security; you NEED antivirus software!
"As Macs have become more popular, more malware has been designed specifically to target those operating systems...people should not feel comfortable saving personal information on their Macs in an unprotected form."
—www.net-security.org
Subscribe to:
Comments (Atom)